1 安装目标
使用源码编译安装 Kubernetes,可以方便的切换版本,方便开发测试工作。本文以 openEuler 24.03 LTS 系统作为基础环境,演示如何操作
2 环境准备
2.1 网络环境
由于编译 docker 所需的源代码资源都在外网,因此需要提前配置代理
# 配置代理
PROXY_IP=192.168.230.1
PROXY_PORT=10809
export http_proxy=http://${PROXY_IP}:${PROXY_PORT}
export https_proxy=http://${PROXY_IP}:${PROXY_PORT}
export ALL_PROXY=http://${PROXY_IP}:${PROXY_PORT}
export all_proxy=socks://${PROXY_IP}:${PROXY_PORT}
# 测试代理
$ curl www.google.com2.2 系统环境
(1)设置主机名及域名解析
# 设置主机名
$ hostnamectl set-hostname k8s-master
# 配置域名解析
$ cat >>/etc/hosts <<EOF
192.168.230.240 k8s-master
EOF(2)关闭防火墙及 SELinux
# 关闭防火墙
$ systemctl stop firewalld && systemctl disable firewalld
# 关闭 SELinux
$ setenforce 0 && sed -i 's/\(SELINUX=\).*/\1disabled/' /etc/selinux/config(3)关闭 Swap 分区
# 关闭 Swap 分区
$ swapoff -a
# 禁止开机自动挂载 Swap 分区
$ sed -i '/swap/ s/^\(.*\)$/#\1/g' /etc/fstab(4)加载 netfilter 模块
# 加载 netfilter 模块
$ modprobe br_netfilter && lsmod | grep br_netfilter
br_netfilter 36864 0
bridge 397312 1 br_netfilter
# 设置开机自动加载 netfilter 模块
$ cat >/etc/modules-load.d/br_netfilter.conf <<EOF
br_netfilter
EOF(5)调整内核参数
# 编写配置文件
$ cat > /etc/sysctl.d/kubernetes.conf <<EOF
net.bridge.bridge-nf-call-ip6tables = 1
net.bridge.bridge-nf-call-iptables = 1
net.ipv4.ip_forward = 1
vm.max_map_count = 262144
EOF
# 加载配置文件
$ sysctl -p /etc/sysctl.d/kubernetes.conf
net.bridge.bridge-nf-call-ip6tables = 1
net.bridge.bridge-nf-call-iptables = 1
net.ipv4.ip_forward = 1
vm.max_map_count = 2621442.3 工具环境
(1)安装编译及其他工具
# 安装编译工具
$ yum install -y gcc-c++ make rsync lxcfs
# 启动 lxcfs
$ systemctl start lxcfs && systemctl enable lxcfs(2)安装 cfssl 工具
# 下载 cfssl 工具
$ wget https://github.com/cloudflare/cfssl/releases/download/v1.6.5/cfssl_1.6.5_linux_amd64 -P /root
# 安装 cfssl 工具
$ mv /root/cfssl_1.6.5_linux_amd64 /usr/local/bin/cfssl && chmod +x /usr/local/bin/cfssl
# 测试 cfssl 工具
$ cfssl version
Version: 1.6.5
Runtime: go1.22.0
# 下载 cfssljson 工具
$ wget https://github.com/cloudflare/cfssl/releases/download/v1.6.5/cfssljson_1.6.5_linux_amd64 -P /root
# 安装 cfssljson 工具
$ mv /root/cfssljson_1.6.5_linux_amd64 /usr/local/bin/cfssljson && chmod +x /usr/local/bin/cfssljson
# 测试 cfssl 工具
$ cfssljson -version
Version: 1.6.5
Runtime: go1.22.02.4 go 环境
(1)配置环境变量
# 配置环境变量
$ cat >> /etc/profile <<"EOF"
export GOPATH=/root/go
export GOBIN=${GOPATH}/bin
export GOROOT=/usr/local/go
export PATH=${PATH}:${GOROOT}/bin
EOF
# 重载环境变量
$ source /etc/profile(2)安装 go 二进制包
# 下载 go 二进制包
$ wget https://golang.google.cn/dl/go1.20.8.linux-amd64.tar.gz -P /root
--2024-12-01 12:47:12-- https://golang.google.cn/dl/go1.20.8.linux-amd64.tar.gz
Connecting to 192.168.230.1:10809... connected.
Proxy request sent, awaiting response... 302 Found
Location: https://dl.google.com/go/go1.20.8.linux-amd64.tar.gz [following]
--2024-12-01 12:47:12-- https://dl.google.com/go/go1.20.8.linux-amd64.tar.gz
Connecting to 192.168.230.1:10809... connected.
Proxy request sent, awaiting response... 200 OK
Length: 100431921 (96M) [application/x-gzip]
Saving to: ‘/root/go1.20.8.linux-amd64.tar.gz’
go1.20.8.linux-amd64.tar. 100%[=============>] 95.78M 11.2MB/s in 8.8s
2024-12-01 12:47:21 (10.9 MB/s) - ‘/root/go1.20.8.linux-amd64.tar.gz’ saved [100431921/100431921]
# 解压二进制包
$ rm -rf /usr/local/go && tar -zxvf go1.20.8.linux-amd64.tar.gz -C /usr/local
# 查看 go 版本
$ go version
go version go1.20.8 linux/amd642.5 容器环境
(1)安装配置 Docker
# 安装 docker
$ yum install -y docker
# 启动 docker
$ systemctl start docker && systemctl enable docker
# 创建服务配置目录
$ mkdir -p /etc/systemd/system/docker.service.d
# 配置代理
$ cat > /etc/systemd/system/docker.service.d/http-proxy.conf <<EOF
[Service]
Environment="HTTP_PROXY=http://${PROXY_IP}:${PROXY_PORT}"
Environment="HTTPS_PROXY=http://${PROXY_IP}:${PROXY_PORT}"
Environment="NO_PROXY=localhost,127.0.0.1"
EOF
# 重新加载配置
$ systemctl daemon-reload
# 重启 docker
$ systemctl restart docker
# 查看代理是否配置成功
$ docker info | grep Proxy
HTTP Proxy: http://192.168.230.1:10809
HTTPS Proxy: http://192.168.230.1:10809
No Proxy: localhost,127.0.0.1
# 测试拉取镜像
$ docker run hello-world
Unable to find image 'hello-world:latest' locally
latest: Pulling from library/hello-world
c1ec31eb5944: Pull complete
Digest: sha256:305243c734571da2d100c8c8b3c3167a098cab6049c9a5b066b6021a60fcb966
Status: Downloaded newer image for hello-world:latest
Hello from Docker!
This message shows that your installation appears to be working correctly.
......(2)安装配置 CRI-Dockerd
2022 年 5 月 3 日,Kubernetes 1.24 版本正式发布,该版本 Kubernetes 正式移除对 Dockershim 的支持(参考文档:Kubernetes容器运行时弃用Docker转型Containerd | i4T)。因此,若还使用 Docker 作为容器运行时,则需要手动安装 CRI-Dockerd,或者使用 Containerd 作为容器运行时(安装方法见附录)
# 下载 cri-dockerd
$ wget https://github.com/Mirantis/cri-dockerd/releases/download/v0.3.15/cri-dockerd-0.3.15.amd64.tgz -P /root
# 解压下载的压缩包
$ tar -xvf /root/cri-dockerd-0.3.15.amd64.tgz
cri-dockerd/
cri-dockerd/cri-dockerd
# 复制命令到 /usr/bin/ 目录,并添加可执行权限
$ cp /root/cri-dockerd/cri-dockerd /usr/bin/ && chmod +x /usr/bin/cri-dockerd
# 编写 cri-docker.service 文件
$ cat > /etc/systemd/system/cri-dockerd.service <<"EOF"
[Unit]
Description=CRI Interface for Docker Application Container Engine
Documentation=https://docs.mirantis.com
After=network-online.target firewalld.service docker.service
Wants=network-online.target
Requires=cri-dockerd.socket
[Service]
Type=notify
ExecStart=/usr/bin/cri-dockerd --network-plugin=cni --pod-infra-container-image=registry.k8s.io/pause:3.8
ExecReload=/bin/kill -s HUP $MAINPID
TimeoutSec=0
RestartSec=2
Restart=always
StartLimitBurst=3
StartLimitInterval=60s
LimitNOFILE=infinity
LimitNPROC=infinity
LimitCORE=infinity
TasksMax=infinity
Delegate=yes
KillMode=process
[Install]
WantedBy=multi-user.target
EOF
# 编写 cri-docker.socket 文件
$ cat > /usr/lib/systemd/system/cri-dockerd.socket <<"EOF"
[Unit]
Description=CRI Docker Socket for the API
PartOf=cri-dockerd.service
[Socket]
ListenStream=%t/cri-dockerd.sock
SocketMode=0660
SocketUser=root
SocketGroup=docker
[Install]
WantedBy=sockets.target
EOF
# 重载配置文件
$ systemctl daemon-reload
# 启动 cri-docker 并设置开机自启
$ systemctl start cri-dockerd && systemctl enable cri-dockerd
Created symlink /etc/systemd/system/multi-user.target.wants/cri-dockerd.service → /etc/systemd/system/cri-dockerd.service.
# 查看 cri-docker 状态
$ systemctl status cri-dockerd
● cri-dockerd.service - CRI Interface for Docker Application Container Engine
Loaded: loaded (/etc/systemd/system/cri-dockerd.service; enabled; preset: disabled)
Active: active (running) since Mon 2024-12-02 08:40:30 CST; 6s ago
TriggeredBy: ● cri-dockerd.socket
Docs: https://docs.mirantis.com
Main PID: 2655 (cri-dockerd)
Tasks: 10
Memory: 10.6M ()
CGroup: /system.slice/cri-dockerd.service
└─2655 /usr/bin/cri-dockerd --network-plugin=cni --pod-infra-container-image=registry.k8s.io/pause:3.8
.....
# 查看套接字文件,调用方法:unix:///run/cri-dockerd.sock
$ ls -l /run/cri-dockerd.sock
srwxr-xr-x 1 root root 0 Dec 2 08:40 /run/cri-dockerd.sock3 编译安装 Kubernetes
3.1 编译 Kubernetes
# 创建存放源代码的目录
$ mkdir -p ${GOPATH}/src/kubernetes
# 进入源代码目录
$ cd ${GOPATH}/src/kubernetes
# 克隆 Kubernetes 源代码
$ git clone https://github.com/kubernetes/kubernetes
Cloning into 'kubernetes'...
remote: Enumerating objects: 1593137, done.
remote: Counting objects: 100% (47/47), done.
remote: Compressing objects: 100% (38/38), done.
remote: Total 1593137 (delta 12), reused 33 (delta 8), pack-reused 1593090 (from 1)
Receiving objects: 100% (1593137/1593137), 1.05 GiB | 16.23 MiB/s, done.
Resolving deltas: 100% (1166449/1166449), done.
Updating files: 100% (26242/26242), done.
# 进入克隆的 Kubernetes 源代码目录
$ cd ${GOPATH}/src/kubernetes/kubernetes
# 查看所有版本分支
$ git ls-remote --tags origin
# 将 Kubernetes 切换到需要的版本
$ git checkout v1.29.11
Updating files: 100% (15331/15331), done.
Note: switching to 'v1.29.11'.
......
# 执行编译命令,编译所有工具
$ KUBE_BUILD_PLATFORMS="$(go env GOHOSTOS)/$(go env GOHOSTARCH)" make all GOFLAGS=-v GOGCFLAGS="-N -l"
# 查看编译生成的命令
$ ls -l ./_output/local/bin/linux/amd64
total 1152540
-rwxr-xr-x 1 root root 61943960 Dec 2 08:55 apiextensions-apiserver
-rwxr-xr-x 1 root root 147363496 Dec 2 08:55 e2e_node.test
-rwxr-xr-x 1 root root 169920112 Dec 2 08:55 e2e.test
-rwxr-xr-x 1 root root 9294084 Dec 2 08:55 ginkgo
-rwxr-xr-x 1 root root 1908996 Dec 2 08:55 go-runner
-rwxr-xr-x 1 root root 48709784 Dec 2 08:55 kubeadm
-rwxr-xr-x 1 root root 59478168 Dec 2 08:55 kube-aggregator
-rwxr-xr-x 1 root root 124129432 Dec 2 08:55 kube-apiserver
-rwxr-xr-x 1 root root 119271576 Dec 2 08:55 kube-controller-manager
-rwxr-xr-x 1 root root 50225304 Dec 2 08:55 kubectl
-rwxr-xr-x 1 root root 48554136 Dec 2 08:55 kubectl-convert
-rwxr-xr-x 1 root root 112603396 Dec 2 08:55 kubelet
-rwxr-xr-x 1 root root 1687704 Dec 2 08:55 kube-log-runner
-rwxr-xr-x 1 root root 110997656 Dec 2 08:55 kubemark
-rwxr-xr-x 1 root root 55877784 Dec 2 08:55 kube-proxy
-rwxr-xr-x 1 root root 56565912 Dec 2 08:55 kube-scheduler
-rwxr-xr-x 1 root root 1605784 Dec 2 08:55 mounter
# 配置环境变量
$ sed -i '$a export PATH=${PATH}:${GOPATH}/src/kubernetes/kubernetes/_output/local/bin/linux/amd64' /etc/profile
# 重载环境变量
$ source /etc/profile
# 测试环境变量是否生效
$ kubeadm version
kubeadm version: &version.Info{Major:"1", Minor:"29", GitVersion:"v1.29.11", GitCommit:"960a2f019319ab5f7ac1c256efcc180a4113343a", GitTreeState:"clean", BuildDate:"2024-12-02T00:49:59Z", GoVersion:"go1.22.8", Compiler:"gc", Platform:"linux/amd64"}说明:
如果只想编译其中一个组件,例如只编译 kubelet,可以使用该命令:
KUBE_BUILD_PLATFORMS="$(go env GOHOSTOS)/$(go env GOHOSTARCH)" make all WHAT=cmd/kubelet GOFLAGS=-v GOGCFLAGS="-N -l"
3.2 安装 etcd
# 进入克隆的 Kubernetes 源代码目录
$ cd ${GOPATH}/src/kubernetes/kubernetes
# 执行安装脚本
$ ./hack/install-etcd.sh
Downloading https://github.com/coreos/etcd/releases/download/v3.5.16/etcd-v3.5.16-linux-amd64.tar.gz succeed
etcd v3.5.16 installed. To use:
export PATH="/root/go/src/kubernetes/kubernetes/third_party/etcd:${PATH}"
# 查看编译生成的命令
$ ls -l third_party/etcd/
total 55180
drwxr-xr-x 3 1000 1000 4096 Sep 11 02:22 Documentation
-rwxr-xr-x 1 1000 1000 23621784 Sep 11 02:22 etcd
-rwxr-xr-x 1 1000 1000 17899672 Sep 11 02:22 etcdctl
-rwxr-xr-x 1 1000 1000 14893208 Sep 11 02:22 etcdutl
-rw-r--r-- 1 1000 1000 42066 Sep 11 02:22 README-etcdctl.md
-rw-r--r-- 1 1000 1000 7359 Sep 11 02:22 README-etcdutl.md
-rw-r--r-- 1 1000 1000 9210 Sep 11 02:22 README.md
-rw-r--r-- 1 1000 1000 7896 Sep 11 02:22 READMEv2-etcdctl.md
# 配置环境变量
$ sed -i '$a export PATH=${PATH}:${GOPATH}/src/kubernetes/kubernetes/third_party/etcd' /etc/profile
# 重载环境变量
$ source /etc/profile
# 测试环境变量是否生效
$ etcd --version
etcd Version: 3.5.16
Git SHA: f20bbad
Go Version: go1.22.7
Go OS/Arch: linux/amd644 使用 Kubernetes
4.1 启动 Kubernetes
# 进入克隆的 Kubernetes 源代码目录
$ cd ${GOPATH}/src/kubernetes/kubernetes
# 修改启动脚本中:允许特权容器运行、API 节点名称
$ sed -i \
-e '/^ALLOW_PRIVILEGED=/c ALLOW_PRIVILEGED=${ALLOW_PRIVILEGED:-"true"}' \
-e '/^HOSTNAME_OVERRIDE=/c HOSTNAME_OVERRIDE=${HOSTNAME_OVERRIDE:-"$(hostname)"}' \
./hack/local-up-cluster.sh
# 若 Kubernetes 版本大于等于 1.24,且使用 Docker 作为容器运行时,则还需要修改容器运行时的套接字
$ sed -i '/^CONTAINER_RUNTIME_ENDPOINT/c CONTAINER_RUNTIME_ENDPOINT=${CONTAINER_RUNTIME_ENDPOINT:-"unix:///run/cri-dockerd.sock"}' ./hack/local-up-cluster.sh
# 执行启动脚本
$ ./hack/local-up-cluster.sh -O
......
To start using your cluster, you can open up another terminal/tab and run:
export KUBECONFIG=/var/run/kubernetes/admin.kubeconfig
cluster/kubectl.sh
Alternatively, you can write to the default kubeconfig:
export KUBERNETES_PROVIDER=local
cluster/kubectl.sh config set-cluster local --server=https://localhost:6443 --certificate-authority=/var/run/kubernetes/server-ca.crt
cluster/kubectl.sh config set-credentials myself --client-key=/var/run/kubernetes/client-admin.key --client-certificate=/var/run/kubernetes/client-admin.crt
cluster/kubectl.sh config set-context local --cluster=local --user=myself
cluster/kubectl.sh config use-context local
cluster/kubectl.sh
------------------------------以下步骤重新打开一个终端执行------------------------------
# 刷新环境变量
$ source /etc/profile
# 声明连接 Kubernetes API 服务器信息的配置文件
$ export KUBECONFIG=/var/run/kubernetes/admin.kubeconfig
# 查看集群节点状态
$ kubectl get node
NAME STATUS ROLES AGE VERSION
k8s-master Ready <none> 10m v1.29.11-dirty4.2 安装 Calico
Calico 下载地址:https://github.com/projectcalico/calico
Calico 版本与 Kubernete 版本需要有对应关系,可参考文档:Documentation archive | Calico Documentation
# 下载 calico
$ wget https://github.com/projectcalico/calico/releases/download/v3.28.2/release-v3.28.2.tgz -P /root
# 解压 calico
$ tar -xvf /root/release-v3.28.2.tgz -C /root
# 加载 calico 镜像
$ for img in $(ls /root/release-v3.28.2/images/*); do docker load -i "${img}"; done
fc72e302317a: Loading layer [==========================>] 3.692MB/3.692MB
17f473a5550b: Loading layer [==========================>] 205.5MB/205.5MB
5f70bf18a086: Loading layer [==========================>] 1.024kB/1.024kB
Loaded image: calico/cni:v3.28.2
4e9f7ac9fb07: Loading layer [==========================>] 38.33MB/38.33MB
Loaded image: calico/dikastes:v3.28.2
3bdcbcc4896a: Loading layer [==========================>] 124.9MB/124.9MB
Loaded image: calico/flannel-migration-controller:v3.28.2
b99a8e25f25e: Loading layer [==========================>] 75.3MB/75.3MB
Loaded image: calico/kube-controllers:v3.28.2
31f1fc200f28: Loading layer [==========================>] 374.2MB/374.2MB
Loaded image: calico/node:v3.28.2
03b5f1752b13: Loading layer [==========================>] 9.832MB/9.832MB
Loaded image: calico/pod2daemon-flexvol:v3.28.2
67c02963f81a: Loading layer [==========================>] 67.58MB/67.58MB
Loaded image: calico/typha:v3.28.2
# 获取 Pod 网络
$ grep "^CLUSTER_CIDR" ${GOPATH}/src/kubernetes/kubernetes/hack/local-up-cluster.sh | awk -F'[-}]' '{print $2}'
10.1.0.0/16
# 修改 yaml 文件,将 CALICO_IPV4POOL_CIDR 修改为获取的 Pod 网络
$ sed -i \
-e '/CALICO_IPV4POOL_CIDR/ s/#\ //' \
-e '/192.168.0.0\/16/ s/#\ //' \
-e "/192.168.0.0\/16/ s/192.168.0.0\/16/10.1.0.0\/16/" \
/root/release-v3.28.2/manifests/calico.yaml
# 启动 calico
$ kubectl apply -f /root/release-v3.28.2/manifests/calico.yaml
# 查看 pod 是否正常运行
$ kubectl get pod -A
NAMESPACE NAME READY STATUS RESTARTS AGE
kube-system calico-kube-controllers-658958974b-m6jn2 1/1 Running 0 29s
kube-system calico-node-4c84x 1/1 Running 0 29s
kube-system coredns-69cbfb9798-hlqvv 1/1 Running 0 5m5s5 如何切换版本
# 进入克隆的 Kubernetes 源代码目录
$ cd ${GOPATH}/src/kubernetes/kubernetes
# 查看所有版本分支
$ git ls-remote --tags origin
# 将 Kubernetes 强制切换到需要的版本
$ git checkout -f v1.31.3
Previous HEAD position was 960a2f01931 Release commit for Kubernetes v1.29.11
HEAD is now at c83cbee114d Release commit for Kubernetes v1.31.3
# 执行编译命令,编译所有工具
$ KUBE_BUILD_PLATFORMS="$(go env GOHOSTOS)/$(go env GOHOSTARCH)" make all GOFLAGS=-v GOGCFLAGS="-N -l"
# 测试新版本命令
$ kubeadm version
kubeadm version: &version.Info{Major:"1", Minor:"31", GitVersion:"v1.31.3", GitCommit:"c83cbee114ddb732cdc06d3d1b62c9eb9220726f", GitTreeState:"clean", BuildDate:"2024-12-02T06:04:02Z", GoVersion:"go1.22.8", Compiler:"gc", Platform:"linux/amd64"}
# 执行 etcd 安装脚本
$ ./hack/install-etcd.sh
Downloading https://github.com/etcd-io/etcd/releases/download/v3.5.15/etcd-v3.5.15-linux-amd64.tar.gz succeed
# 测试新版本命令
$ etcd --version
etcd Version: 3.5.15
Git SHA: 9a5533382
Go Version: go1.21.12
Go OS/Arch: linux/amd64
# 必须删除 cni 插件,否则会导致 coredns 启动失败。详见 6(2)
$ rm -rf /opt/cni
# 后续按照第 4 章中的方法启动即可6 FAQ
(1)/root/go/src/kubernetes/kubernetes/_output/local/.gimme/versions/go1.22.8.linux.amd64/pkg/tool/linux_amd64/link: mapping output file failed: no space left on device
问题现象:
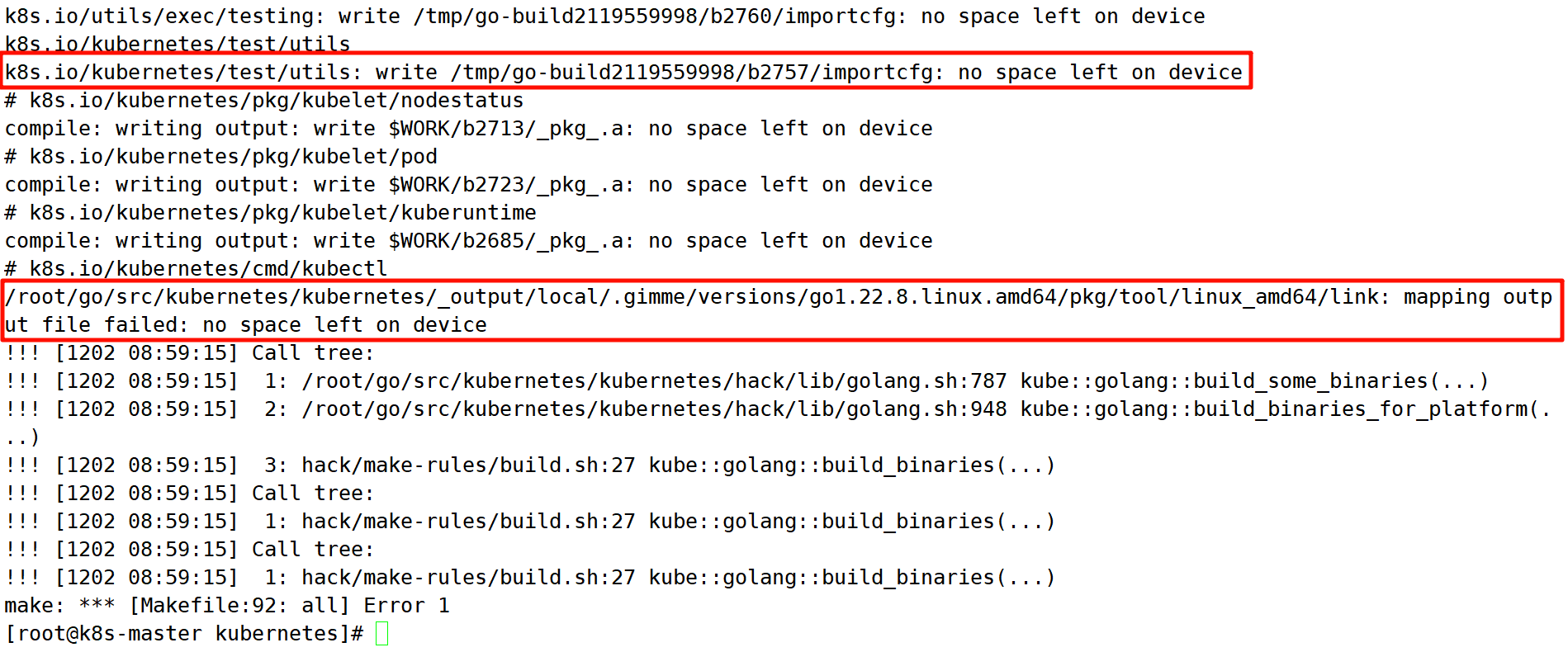
问题原因:
编译过程中需要向 /tmp 目录写入临时文件,但该目录空间不足
解决方案:
若 /tmp 为单独挂载的 tmpfs 文件系统。则将其卸载:
# 查看 /tmp 是否挂载
$ df -Th /tmp
Filesystem Type Size Used Avail Use% Mounted on
tmpfs tmpfs 2.7G 66M 2.6G 3% /tmp
# 卸载 /tmp
$ umount -fl /tmp(2)切换分支后,coredns 启动失败
问题现象:
执行 kubectl describe pod -n kube-system coredns-*-* 命令,看到包含类似如下报错:
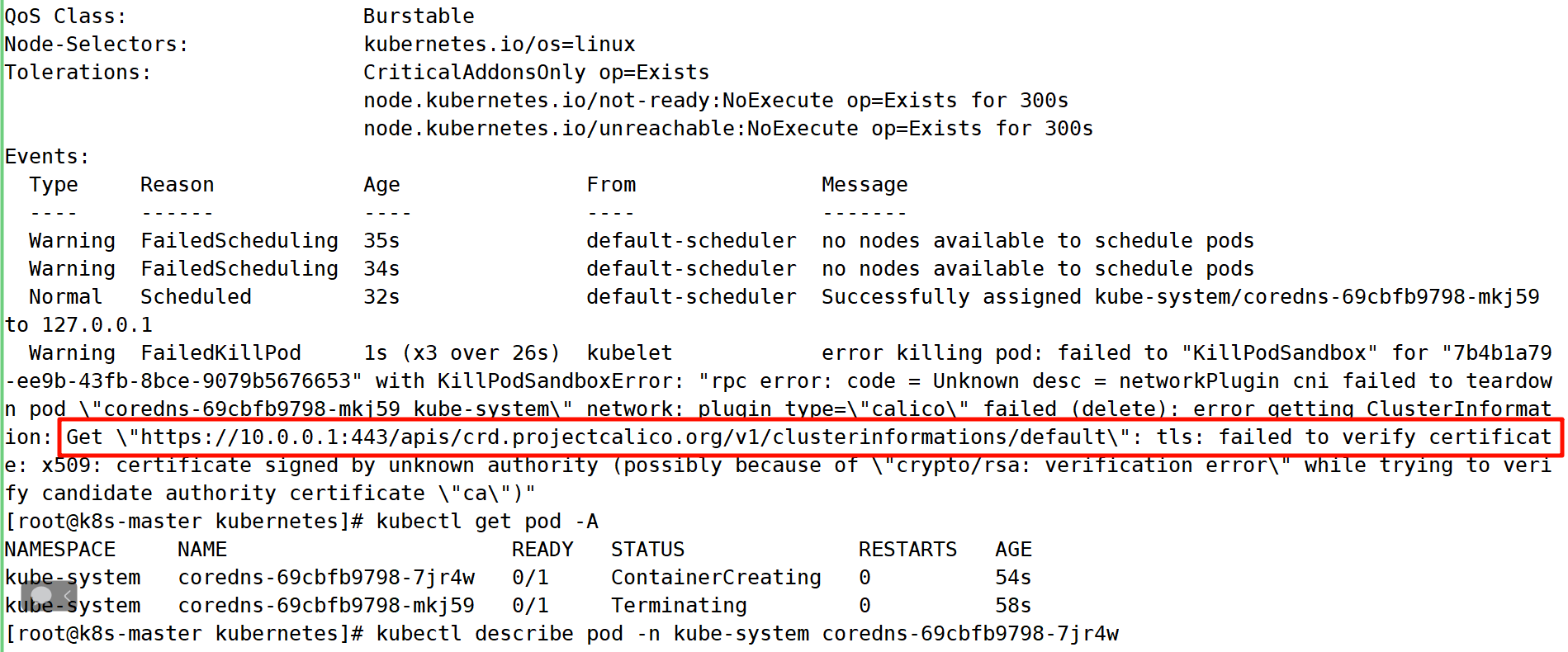
问题原因:
切换版本后,cni 插件不兼容,导致网络有问题
解决方案:
每次切换版本,都要及时删除 cni 插件:
$ rm -rf /opt/cni附录 部署 Containerd
# 下载 containerd 包
$ wget https://github.com/containerd/containerd/releases/download/v1.7.15/cri-containerd-cni-1.7.15-linux-amd64.tar.gz -P /root
# 将下载的包解压到根目录中,压缩包自带目录结构
$ tar -xvf /root/cri-containerd-cni-1.7.15-linux-amd64.tar.gz -C /
# 创建配置文件目录
$ mkdir /etc/containerd
# 生成配置文件
$ containerd config default > /etc/containerd/config.toml
# 配置 systemdcgroup 驱动程序
$ sed -i '/SystemdCgroup/ s/false/true/' /etc/containerd/config.toml
# 更新runc,因为cri-containerd-cni-1.6.6-linux-amd64.tar.gz的runc二进制文件有问题,最后说明。这一步很重要 ✰ ✰ ✰
# wget https://github.com/opencontainers/runc/releases/download/v1.1.3/runc.amd64
# mv runc.amd64 /usr/local/sbin/runc
# mv:是否覆盖"/usr/local/sbin/runc"? y
# chmod +x /usr/local/sbin/runc
# 创建服务配置目录
$ mkdir -p /etc/systemd/system/containerd.service.d
# 配置代理
$ cat > /etc/systemd/system/containerd.service.d/http-proxy.conf <<EOF
[Service]
Environment="HTTP_PROXY=http://${PROXY_IP}:${PROXY_PORT}"
Environment="HTTPS_PROXY=http://${PROXY_IP}:${PROXY_PORT}"
Environment="NO_PROXY=localhost,127.0.0.1"
EOF
# 重新加载配置
$ systemctl daemon-reload
# 启动 containerd 服务并设置开机自启
$ systemctl start containerd && systemctl enable containerd
Created symlink /etc/systemd/system/multi-user.target.wants/containerd.service → /etc/systemd/system/containerd.service.
# 查看 containerd 服务状态
$ systemctl status containerd
● containerd.service - containerd container runtime
Loaded: loaded (/etc/systemd/system/containerd.service; enabled; preset: disabled)
Active: active (running) since Mon 2024-12-02 08:54:44 CST; 19s ago
Docs: https://containerd.io
Main PID: 3129 (containerd)
Tasks: 12
Memory: 10.6M ()
CGroup: /system.slice/containerd.service
└─3129 /usr/local/bin/containerd
......
# 测试拉取镜像
$ ctr image pull docker.io/library/hello-world:latest
docker.io/library/hello-world:latest: resolved |++++++++++++++++++++++++++++++++++++++|
index-sha256:305243c734571da2d100c8c8b3c3167a098cab6049c9a5b066b6021a60fcb966: done |++++++++++++++++++++++++++++++++++++++|
manifest-sha256:e2fc4e5012d16e7fe466f5291c476431beaa1f9b90a5c2125b493ed28e2aba57: done |++++++++++++++++++++++++++++++++++++++|
config-sha256:d2c94e258dcb3c5ac2798d32e1249e42ef01cba4841c2234249495f87264ac5a: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:c1ec31eb59444d78df06a974d155e597c894ab4cda84f08294145e845394988e: done |++++++++++++++++++++++++++++++++++++++|
elapsed: 5.1 s total: 14.4 K (2.8 KiB/s)
unpacking linux/amd64 sha256:305243c734571da2d100c8c8b3c3167a098cab6049c9a5b066b6021a60fcb966...
done: 29.001739ms
# 查看套接字文件,调用方法:unix:///run/containerd/containerd.sock
$ ls -l /run/containerd/containerd.sock
srw-rw---- 1 root root 0 Dec 2 09:15 /run/containerd/containerd.sock



评论